Infosecinstitute CTF 2 - LEVEL 5
This will be solution for Level 5 Practical Web Hacking CTF #2.
In this Level is about access controls, this vulnerability happeds when an application either has bad access control implementation, the most common is related to session management, issues like the use of md5 or any other depercated week hashing algorithm, unsafe random. Im both cases the application follows the execution without proper validation, Access control.
In this case the objective is to make the server assume that i’m valid and autheticated user.
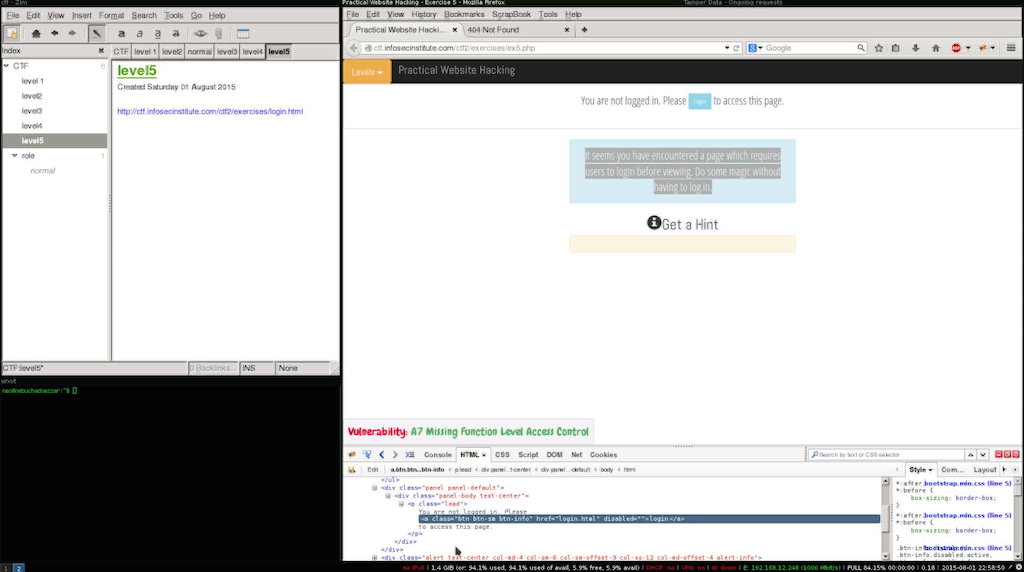
This vulnerabilities are very easy to exploit and very common, for this types for vulnerabilites my usual check list is as folows:
- Check for week sessions and\or depercated hashing algorithms.
- Session id guessing.
- Credetial guessing \ bruteforce.
- Redirects
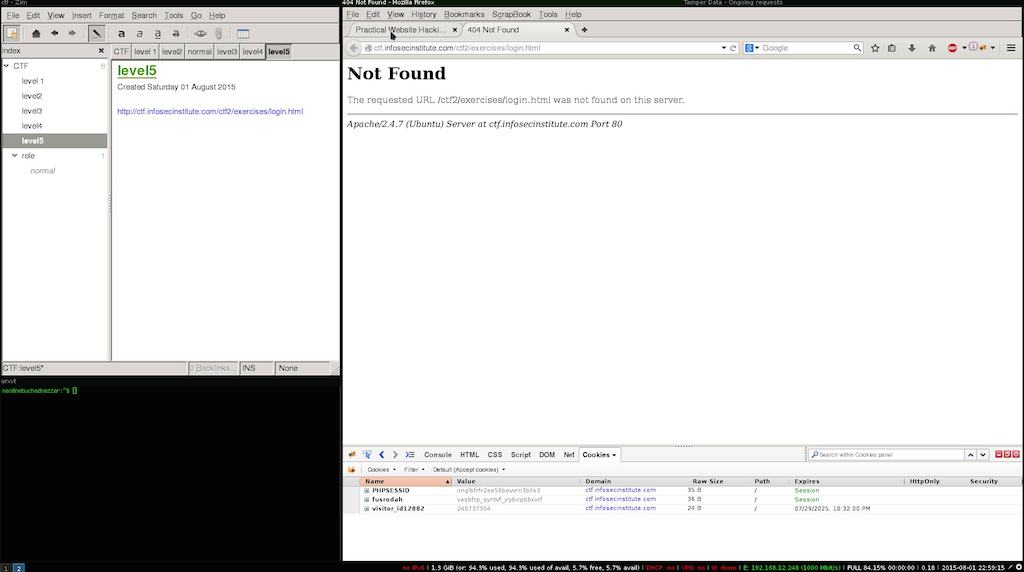
After the initial inspection where i tryed to access the login.html page contained on the disabled login button i noticed that it doen’t exist. this excludes options 2 and 3 and leaves us with one and 1 and 4 i decided to go with the last one.
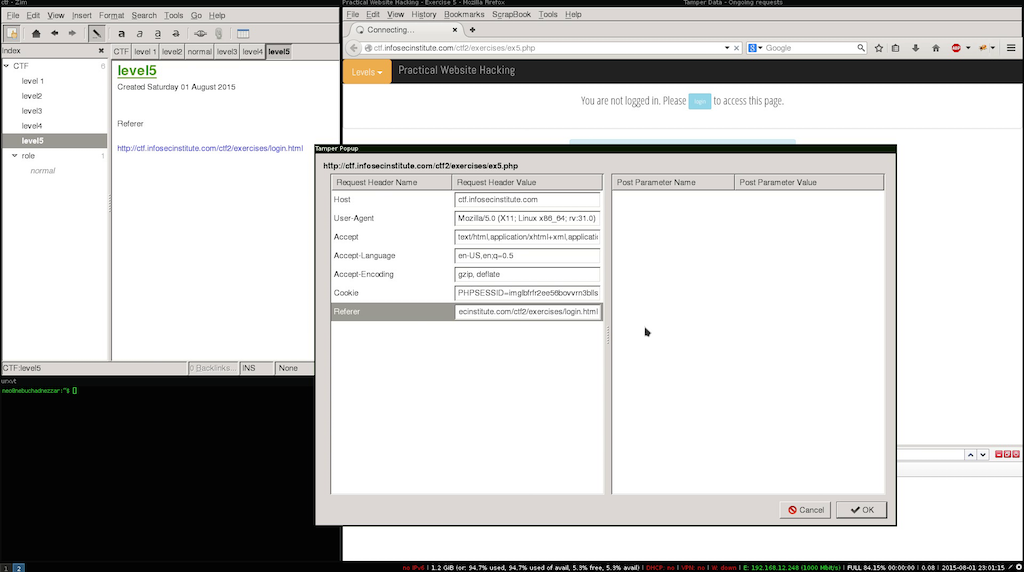
Tasks
- Execute a Get Request.
- Intercept the get Request before its sent of to the serve.
- Add http referer header to.
- Sumit and verify.
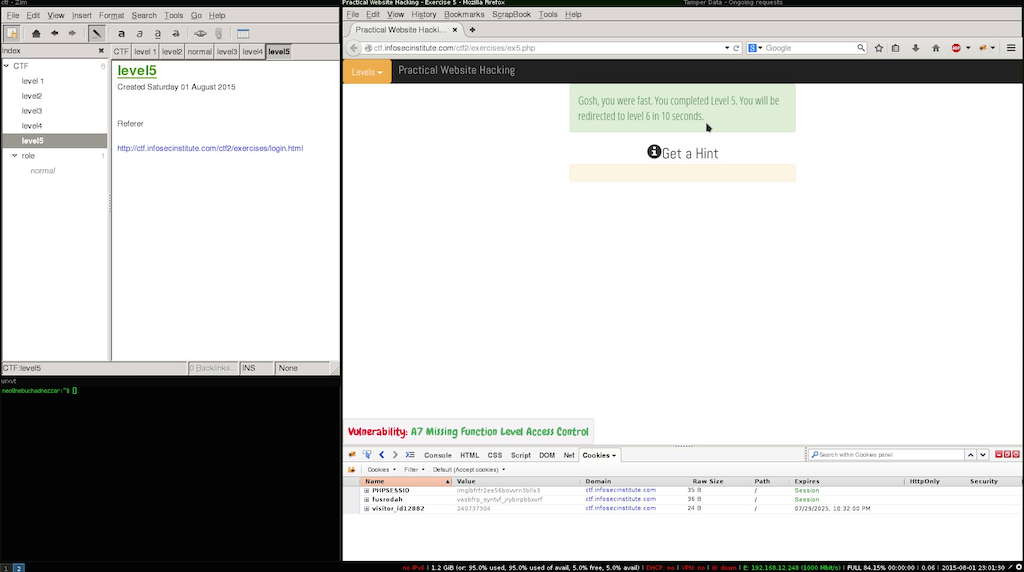
Success!